I recently tried to explain the concept of Split-Brain DNS to a colleague, with little success. Unless you are heavily involved in the infrastructure side of IT, the nuances of DNS can be daunting to the uninitiated.
Split-Brain DNS, also known as “Split-Horizon DNS” attempts to solve a problem that arises when any kind of network resource must be accessed from both inside and outside of a network.
For example, let’s say an IP-based video surveillance system has been set up at your workplace. All cameras feed into a device called an NVR, or Network Video Recorder. One feature of devices like this is that you can access the video feed from a computer or a mobile device like a tablet or phone. Just like any network resource like server or printer, to reach the NVR to view the video feed, you must know the address of the NVR. For the purposes of this example, we’ll say that the device address is 192.168.0.50. This is where the problem starts: this address will only work while inside the network. As soon as you leave the premises, no longer connected wired or wirelessly to the internal network, you can no longer reach the NVR by that address, not just because of the firewall, but also because the addresses in the 192.168.0.* network can’t be reached directly from the public internet space.
What many will do, then, is configure multiple profiles: one for internal use, another for outside. But what if you wanted to access the NVR with a single friendly server name, from both inside and outside the network?
Although this involves a little more on the infrastructure side, I’m a strong believer in making things simpler for users and clients. In my experience, a lot of confusion can arise from not being able to access this kind of information from a single profile.
So to understand split brain DNS, I need to delve a little into what Domain Name System (DNS) is and how it works.
DNS is basically a system that correlates an easy to remember name with a not easy to remember IP address. When you type in ” www.google.ca”, a bunch of things happen behind the scenes: your computer asks another computer where www.google.ca is, and eventually in a matter of a few thousandths of a second, the public address of that server is returned. You the user never see what that IP address is unless you know how to look for it, because everything happens invisibly and is handled by your browser and computer. See also my earlier post What is DNS?.
In this example, Google maintains a “DNS zone”, which is basically just a list of servers and server names that are publicly addressable.
Most businesses will have a website, which means that they will have a DNS zone for that domain. To properly configure split brain DNS, all one needs is a domain name, and an internal DNS server.
I will use my own website as an example. My website at www.mcleanit.ca is hosted on a Web server in California. In my DNS zone (mcleanit.ca) there is a server named “WWW”, whose value is the IP address of my Web server. When you look up www.mcleanit.ca, this is where it finds the real IP address and returns it to your computer. But I could have other servers. I might have a billing.mcleanit.ca, or mail.mcleanit.ca.
To continue the earlier example of the video surveillance system, I could make a DNS record called “surveillance” and point it at my (ideally static) public address of my place of business. From there, I would have to open up the relevant ports in the firewall and redirect them to the NVR. This would allow me to access the NVR remotely while outside of the network using surveillance.mcleanit.ca.
Here is where Split-Brain DNS comes in. A private local network can have its own DNS server. Often it is used in larger networks when servers and other network resources need to be addressed by name easily. Maybe an internal tracking system or private intranet website.
On the local DNS server, I could create another DNS zone for mcleanit.ca identical to the first, except for resources that exist on the local network, which I would instead correlate to the internal address. Then I would configure the DHCP server to assign the internal DNS server as the primary DNS provider. So while the real, public DNS record for surveillance.mcleanit.ca would point at my public address, the internal DNS record would override that with the local address for all internal computers (all those configured by DHCP, at least). Attempts to reach surveillance.mcleanit.ca from either inside or outside of the local network will now reach the same destination: the NVR.
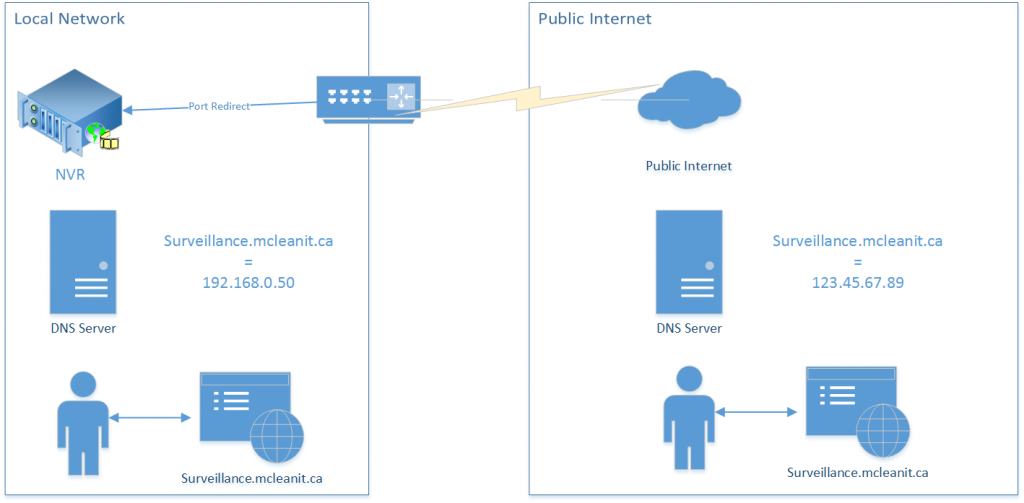
The downside is that now both DNS zones will have to be maintained. Changes to the public DNS zone will have to be duplicated on the private one when appropriate.
Implementing a DNS server doesn’t need a big expensive server though. A perfect use-case scenario even for home users is to make a Synology NAS available both inside and outside a network. And even the single-drive units themselves support Synology’s DNS app for an easy-to-use interface.
Leave a Reply
You must be logged in to post a comment.